Intro to Managing Secrets
Intro to Managing Secrets
As organizations increasingly rely on Rundeck, it becomes crucial to prioritize the secure storage of cryptographic keys. Proper key storage practices are fundamental to safeguarding sensitive information, protecting critical systems, and reinforcing the overall security posture. By consolidating keys in a centralized repository, organizations can enforce consistent security policies, control access, monitor key usage, and maintain audit logs.
Rundeck utilizes built-in key storage to save all credentials related to remote nodes (or for other purposes). Also, it’s possible to integrate with other top secret management technologies like Hashicorp Vault, Cyberark Privileged Access, and Thycotic Secret Server.
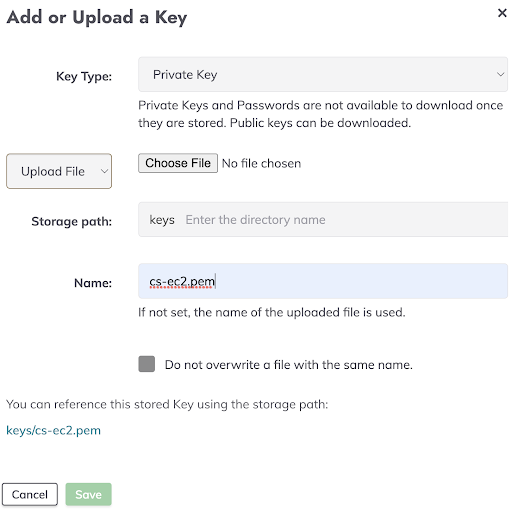
The interface to upload a key to the Rundeck keystore
Storage Options in Rundeck and Runbook Automation
Rundeck Key Storage
Rundeck Key Storage is the space that Rundeck Admins can use to store current sensitive private key/password data ("keys") storage that can be utilized across Rundeck. By default, Rundeck stores these keys on the internal backend database. These keys can be used to customize the automation environment's plugins, node executors, and other components.
Rundeck also has Key Storage Encryption. This enables the encryption of keys and passwords saved on the Rundeck Key Storage (at the Rundeck backend). The following setting allows this encryption and is predefined in the rundeck-config.properties file:
# Encryption for key storage
rundeck.storage.provider.1.type=db
rundeck.storage.provider.1.path=keys
rundeck.storage.converter.1.type=jasypt-encryption
rundeck.storage.converter.1.path=keys
rundeck.storage.converter.1.config.encryptorType=custom
rundeck.storage.converter.1.config.password=encryption_password
rundeck.storage.converter.1.config.algorithm=PBEWITHSHA256AND128BITAES-CBC-BC
rundeck.storage.converter.1.config.provider=BC
Hashicorp Vault Integration
HashiCorp Vault is a highly regarded open-source tool that provides a centralized and secure solution for managing secrets, encryption keys, and sensitive data in modern IT environments. Acting as a robust secrets management platform, Vault offers a wide range of features including secret storage, dynamic secret generation, secure access controls, and encryption as a service.
Additional Storage Options in PagerDuty Runbook Automation
Thycotic Secret Server Integration
Thycotic Secret Server is a Privileged Access Management (PAM) solution designed to secure and streamline the management of sensitive secrets and privileged credentials within organizations. It provides a centralized repository for storing and managing secrets, including passwords, SSH keys, database credentials, and API tokens.
Cyberark Privileged Access Integration
CyberArk is a provider of privileged access security solutions, offering a comprehensive suite of products designed to protect and manage privileged accounts, credentials, and secrets within organizations. CyberArk's flagship product, CyberArk Privileged Access Security, helps organizations secure, monitor, and control privileged access to critical systems and data.
How does Key Storage work with third-party tools?
If using a third-party secrets tool, it is possible to use that keystore in addition to or instead of the built-in keystore. Rundeck abstracts the key provider’s backend to efficiently store or retrieve passwords, public keys, and secret keys directly in the Rundeck interface but stored in the third-party store.
Practical Example: How to use a Secret to authenticate against remote nodes
The linked example walks through configuring a remote SSH node, providing a good example for learning how to store keys and how to reference them in model sources to dispatch commands.
