AWS Secrets Manager
AWS Secrets Manager
Available in PagerDuty Runbook Automation Commercial products.
AWS Secrets Manager allows users to manage, retrieve, and rotate database credentials, application credentials, OAuth tokens, API keys, and other secrets throughout their life-cycles. Many AWS services store and use secrets in Secrets Manager.
This integration allows users to retrieve secrets from the AWS Secrets Manager service and use those secrets for connecting to resources such as VMs, databases, other tools, and much more.
Setup
Authentication
The AWS Secrets integration uses authentication set through the AWS Plugin within System Configuration. If this is already configured, continue on to the next section.
Otherwise, follow the instructions here and choose the auth type that aligns with your Runbook Automation deployment type.
IAM Permissions
The following permissions are required for the AWS Secrets Manager integration to retrieve secrets:
secretsmanager:ListSecretssecretsmanager:GetSecretValue
Here is an example IAM policy that can be attached to the IAM Role that is used for the AWS Secrets Manager integration:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:ListSecrets"
],
"Resource": "*"
}
]
}
Optionally, also use the following permissions to add, update or delete secrets:
secretsmanager:PutSecretValuesecretsmanager:UpdateSecretsecretsmanager:DeleteSecret
Configuration
- Navigate to the System Menu (gear icon in the upper right).
- Click on Key Storage.
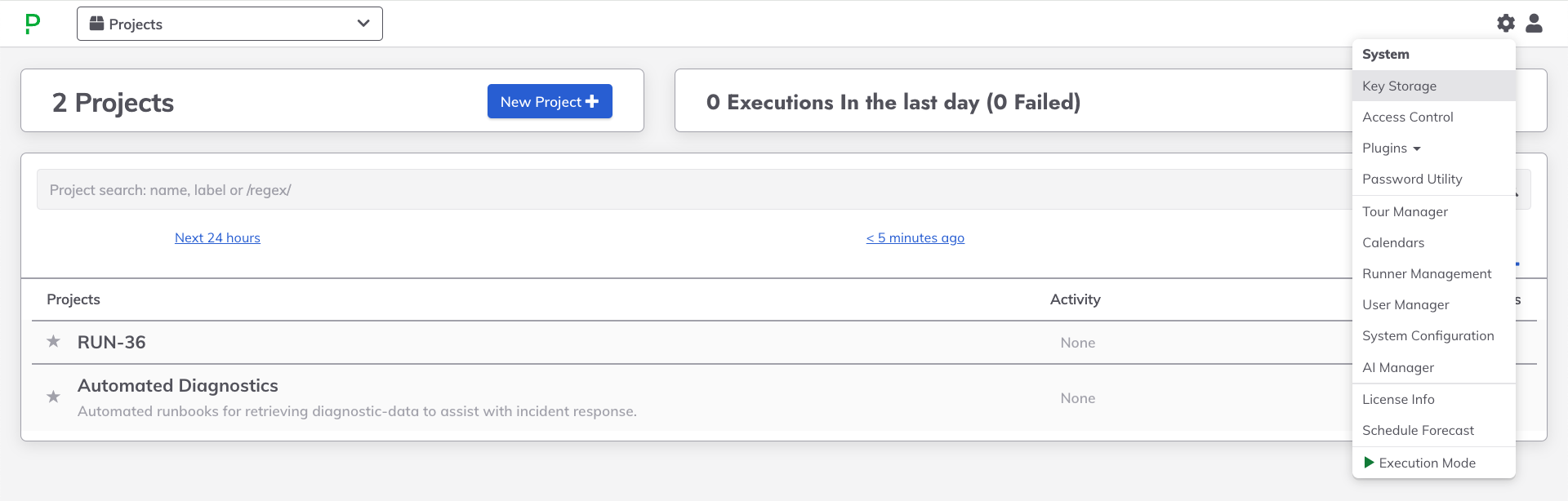
- Navigate to the Configure tab.
- Click on Add Storage Plugin +.
- Click on AWS Secrets Manager from the popup list.
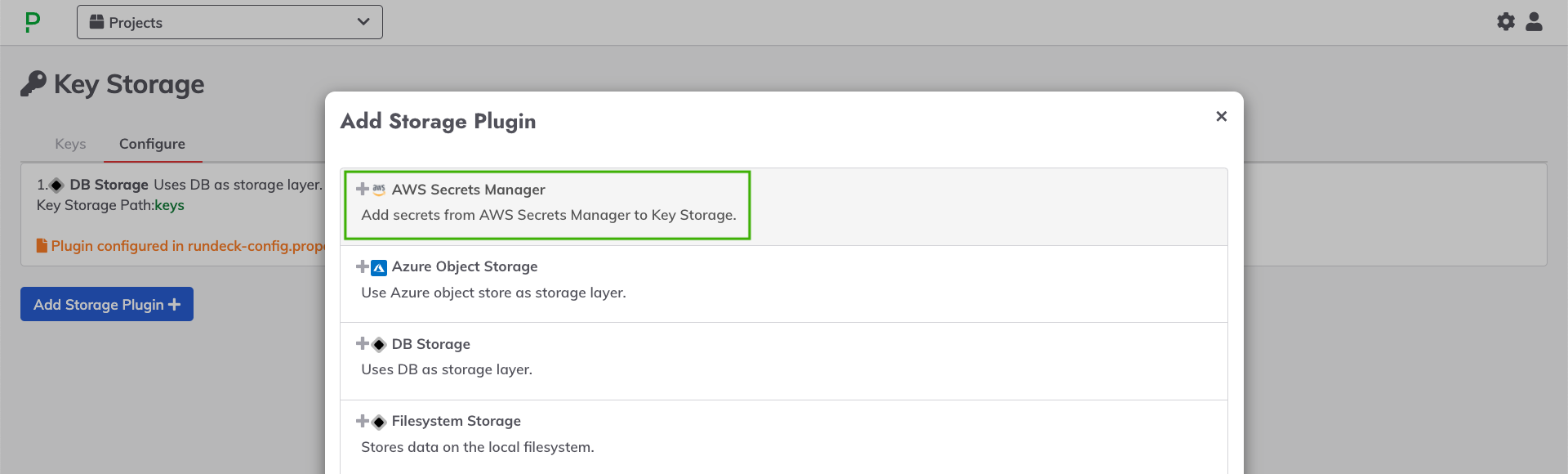
- In the Key Storage Path field, type in a directory name to be the "root" for the secrets retrieved from AWS. For example,
keys/aws-secretswould create a directory calledaws-secretswithin the basekeysdirectory of the Key Storage tree. - Click the checkbox for Remove Path Prefix
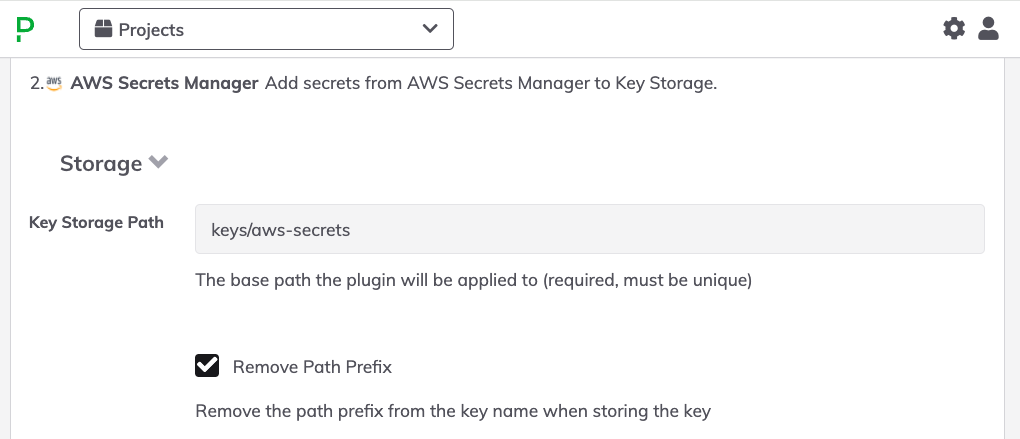
- Optionally set an IAM Role ARN in the Assume Role ARN field.
When to set Assume Role ARN
By default, the AWS Secrets Manager integration authenticates with AWS through the credentials set in the AWS plugin within System Configuration. This means that secrets will be retrieved from the AWS account that is configured through the AWS plugin. In order to retrieve AWS Secrets from multiple AWS accounts, then place the IAM ARN from the "external" account into the Assume Role ARN field.
- Optionally use the Access Key and Secret Key for authentication.
Not Recommended for Production
Amazon firmly states that the Access Key and Secret Key method of authentication should only be used for testing purposes and should not be used for any production use-cases. For more information, click here.
- Select the Regions where the secrets are stored in AWS Secrets Manager.
- If multiple regions are selected, then the integration will retrieve secrets from all selected regions.
- Optionally choose to include or exclude secrets that contain a specific substring.
- Click Save to commit changes for the integration.
- Click Save to add this integration to the Key Storage configuration.
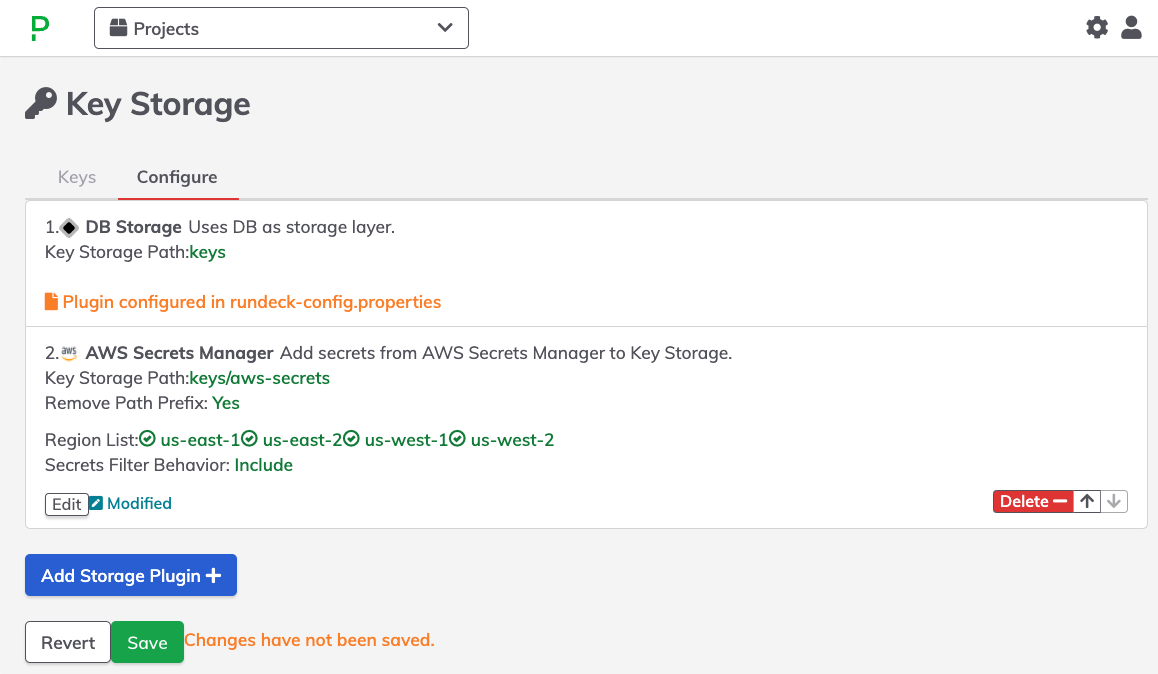
Within the Keys tab, refresh the browser page and the new directory path specified in Step 6 should appear:
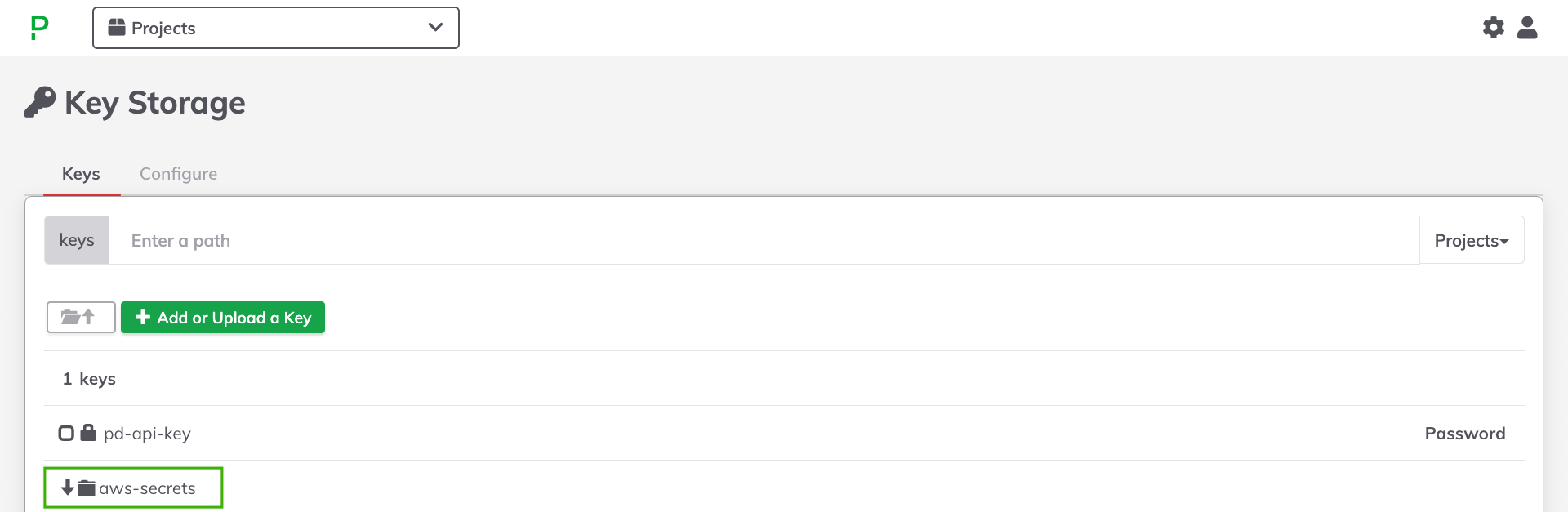
Click into this directory and begin to navigate the secrets retrieved from AWS Secrets Manager.
Usage
Once the integration is configured, the secrets from AWS Secrets Manager can be used by the various functions of the Runbook Automation product that require secrets.
Directories within Key Storage
In order to make it easier to browse the secrets from AWS Secrets Manager, keys with forward-slashes / will be grouped into directories. For example, if there is a secret in AWS with the name
kubernetes/clusters/api-token-12345, then in Runbook Automation this will result in a directory kubernetes with a sub-directory clusters and then a key with the name api-token-12345.
When multiple key-values pairs reside in a single AWS Secret, all keys are available within Key Storage in Runbook Automation: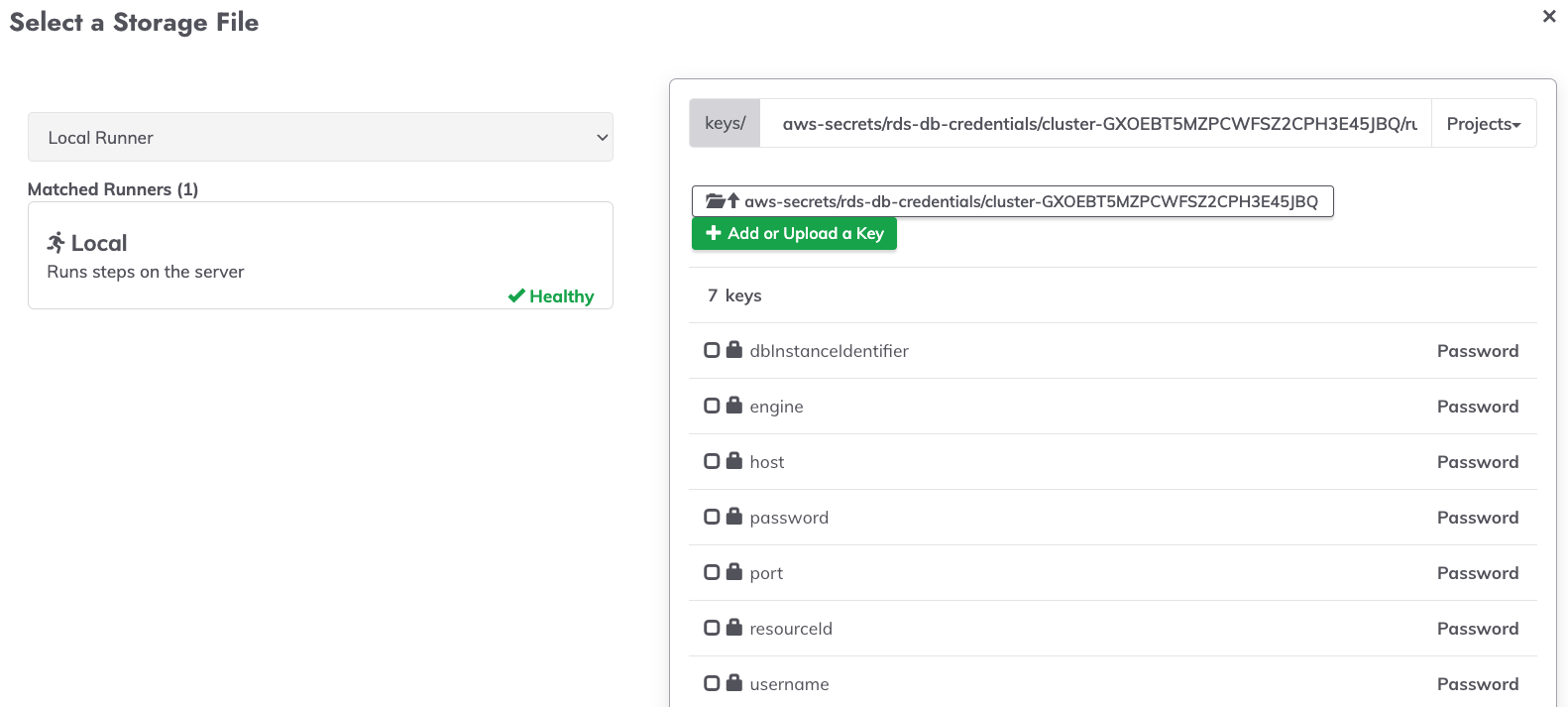
Example Use Cases
Example: SSH Key for Connecting to Nodes
In this example, there is an SSH Key in AWS Secrets Manager: 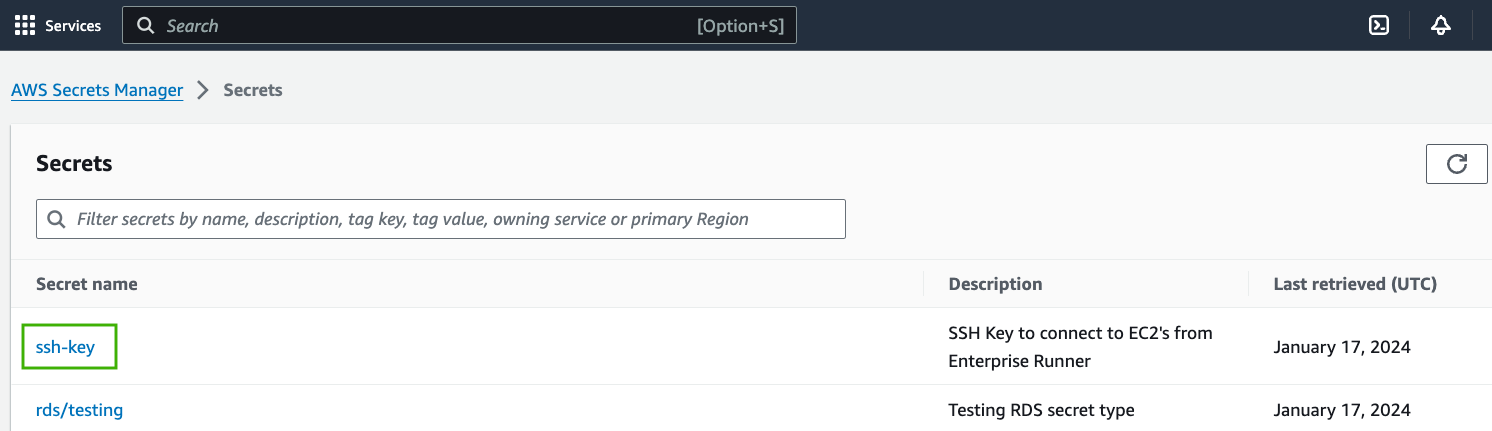
To use this secret and the SSH Key for connecting to nodes:
- Within the Project inside Runbook Automation, navigate to Project Settings -> Edit Configuration:
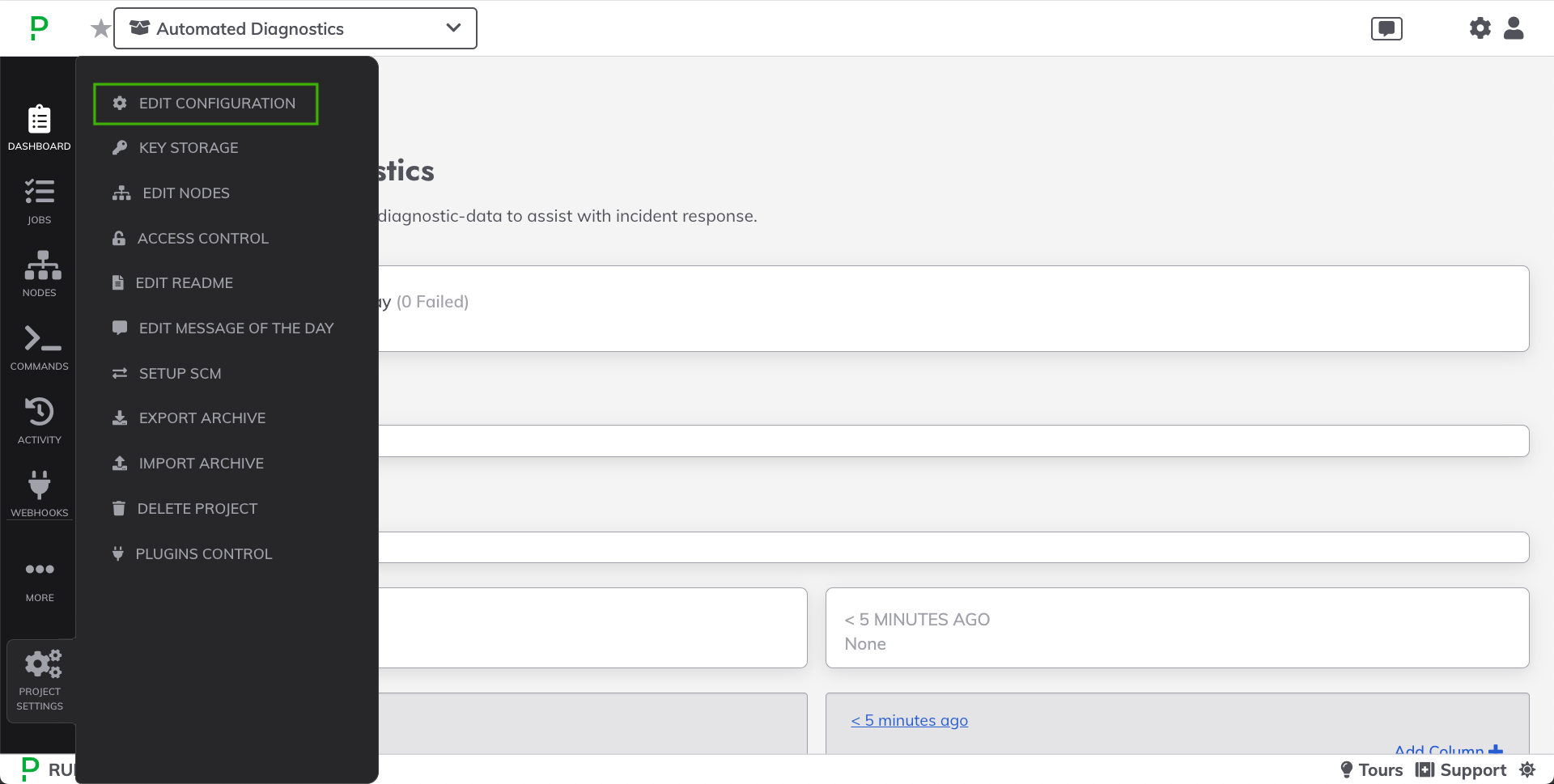
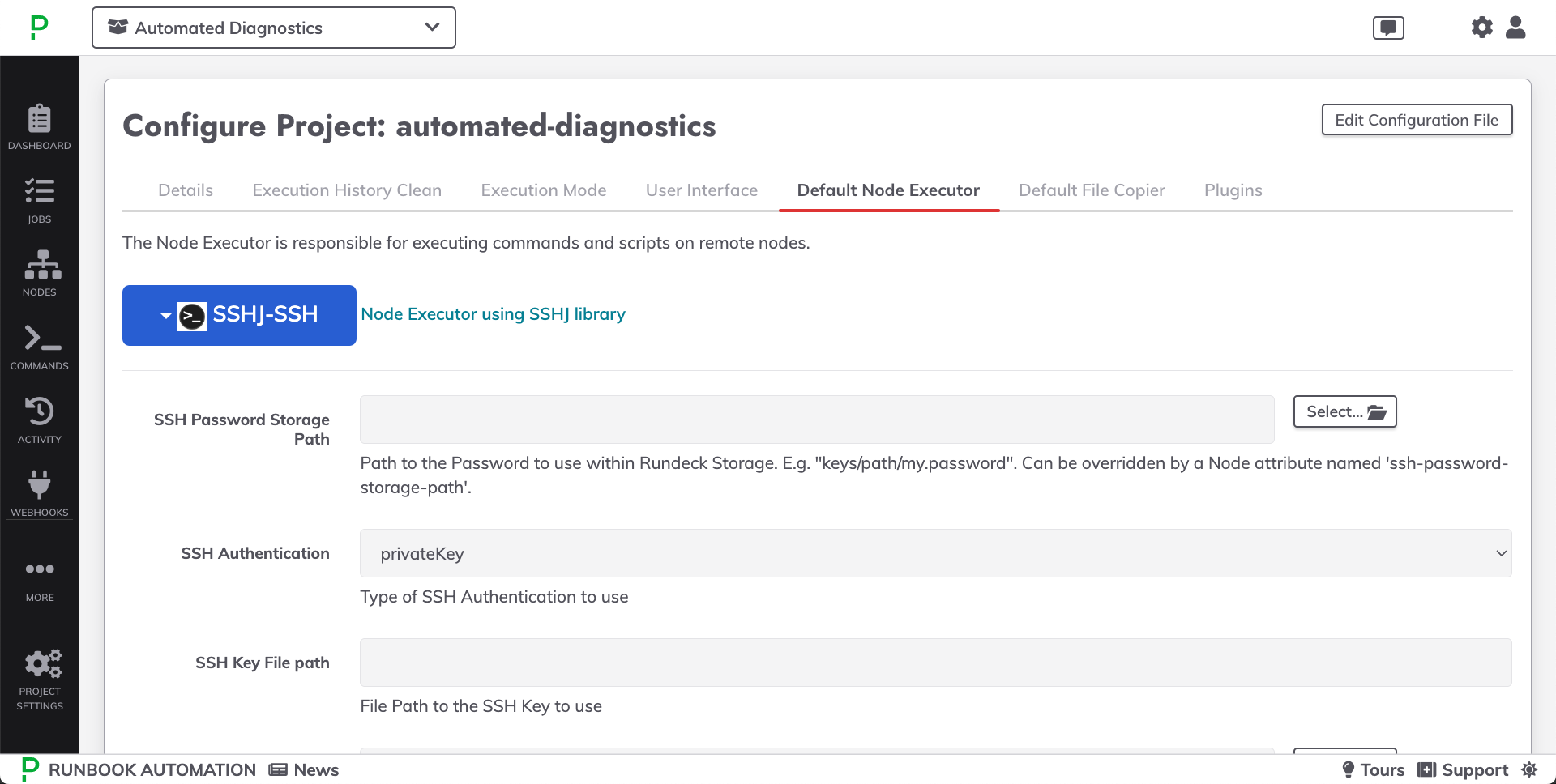
- Click on the Default Node Executor tab.
- From the dropdown, select SSHJ-SSH:
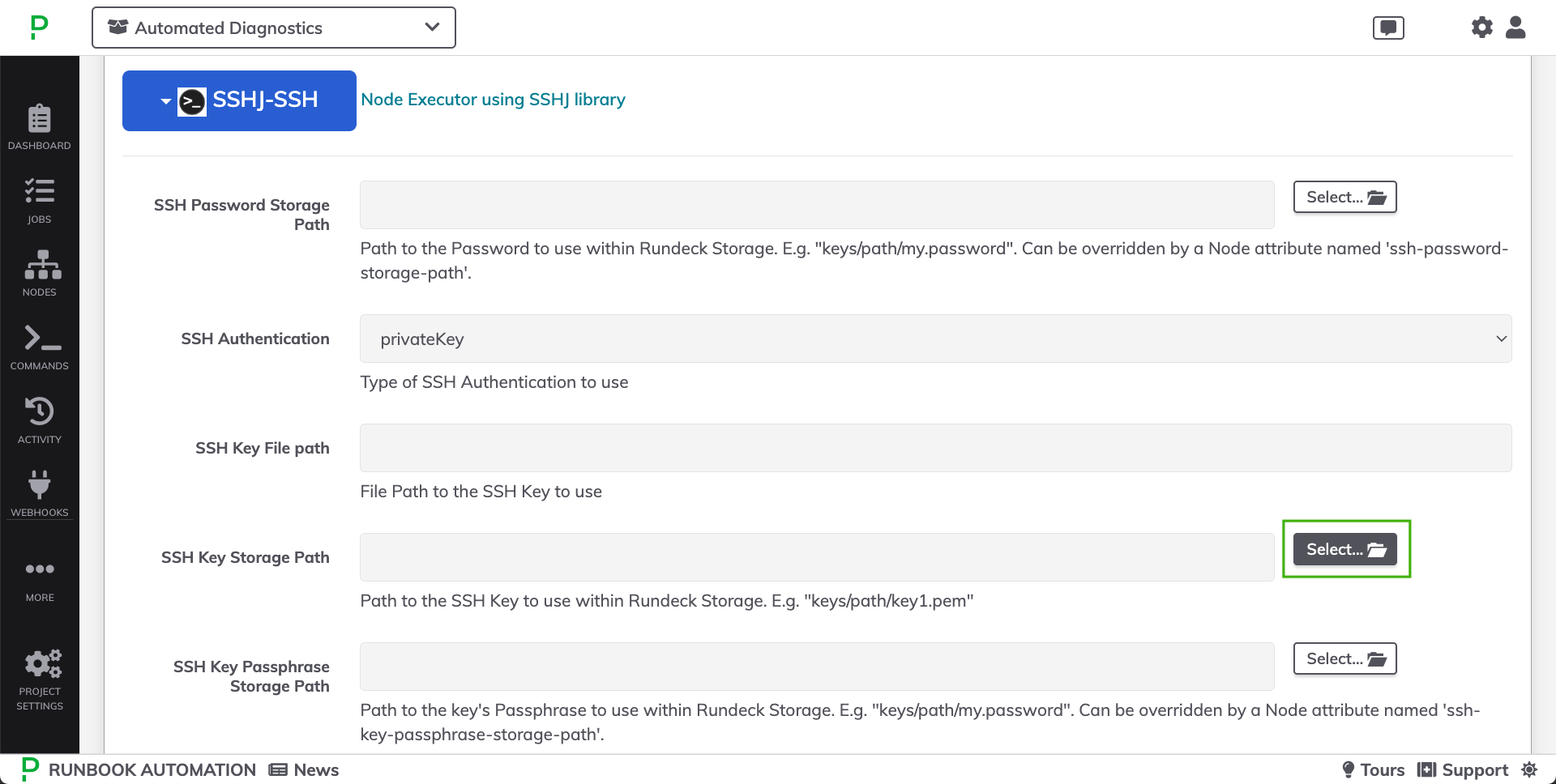
- Click Select... next to the SSH Key Storage Path field:
- From within the popup, click on the folder that was configured for AWS Secrets Manager (in the prior section, the example used was
aws-secrets):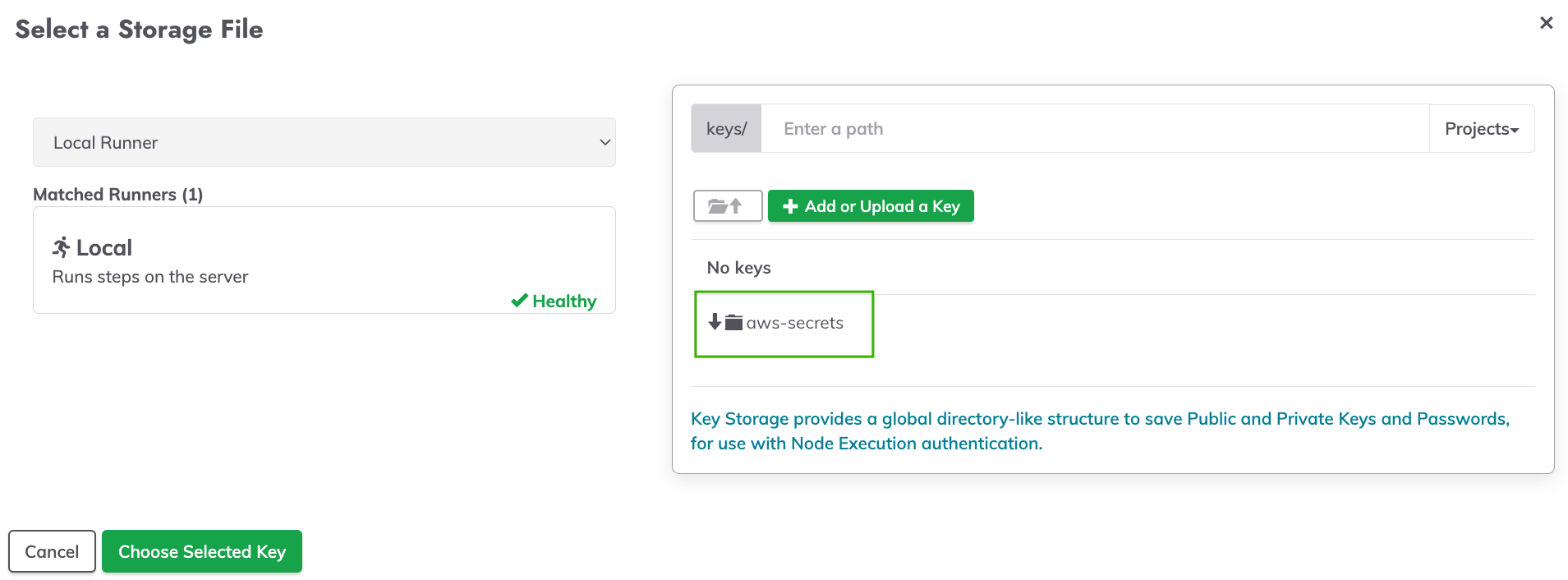
- Within this folder, select the SSH Key for the Node Executor.
- Click Choose Selected Key.
- Click Save at the bottom of the Node Executor configuration.
Example: Database Password for RDS Instance
In AWS Secrets Manager, secrets can have multiple key-value pairs. This is the case for the RDS Credentials type of secret: 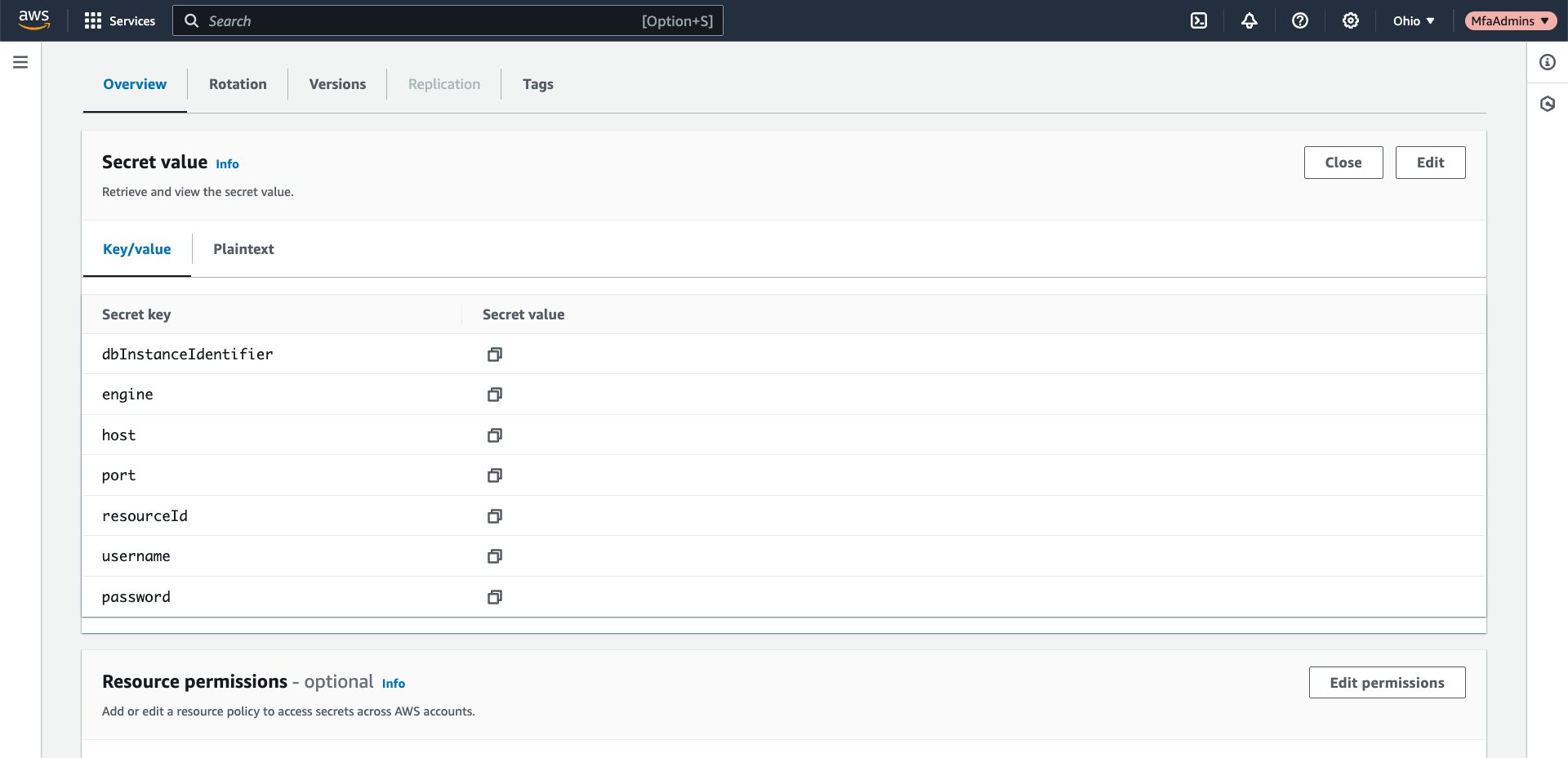
This example assumes that you already have an Enterprise Runner installed in a security group that can connect to the RDS database or that the self-hosted software has a direct path to the RDS database.
- Within the Project inside Runbook Automation, navigate to Jobs.
- Click + New Job.
- Give the Job a name - such as Query RDS Database.
- Click into the Workflow Tab.
- In the Search Step field, type in
SQL. - Click on SQL Run Step.
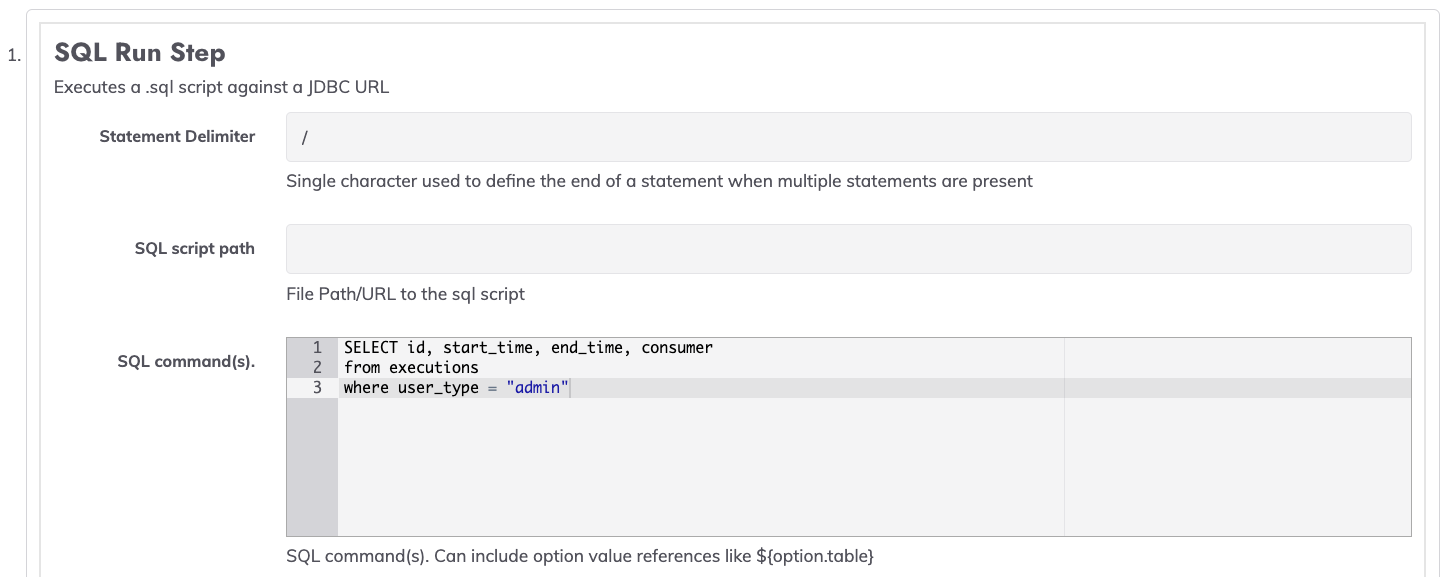
- In the SQL Command(s) box, type in the SQL query to execute against the database:
- Type in the JDBC Driver class name that matches the type of RDS instance:
- MySQL or MariaDB:
org.mariadb.jdbc.Driver(also Aurora compatible) - MS SQL:
com.microsoft.sqlserver.jdbc.SQLServerDriver - Postgres:
org.postgresql.Driver(also Aurora compatible) - Oracle:
oracle.jdbc.OracleDriver
- MySQL or MariaDB:
- In the JDBC url field, type in the connection string with the following format:
jdbc:mysql://db-name.cj3ixhryi3fb.us-west-2.rds.amazonaws.com:3306/db-name - Type in the username to connect to the database.
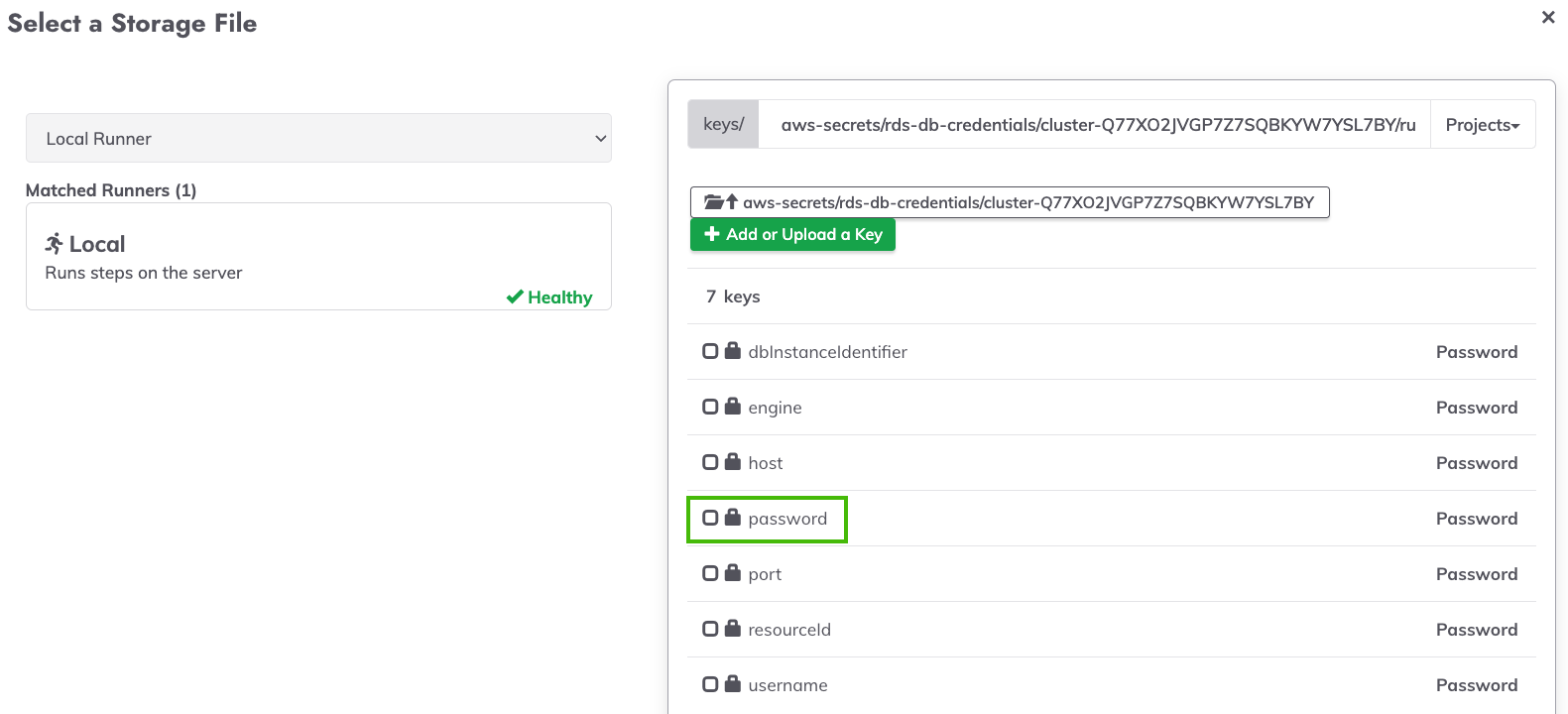
- Click Select... next to the Password from key storage field.
- Navigate through the directories of the RDS keys in AWS Secrets manager.
- Select the password key from the list of secrets:
- Click Choose Selected Key.
- Click Save for the step.
- Navigate into the Node & Runners tab and use the Runner Set selector to choose the Runner that is installed in the AWS Security group with access to the RDS database.
